Overview
A vulnerability exists in the SISCO OSI stack for Windows. If successfully exploited, an attacker could cause a denial-of-service condition.
Description
Inter-control Center Communications Protocol (ICCP) The Inter-control Center Communications Protocol (ICCP) is a protocol that is used to communicate data between control centers that operate SCADA networks. |
Impact
A remote, unauthenticated attacker may be able to cause a denial-of-service condition. |
Solution
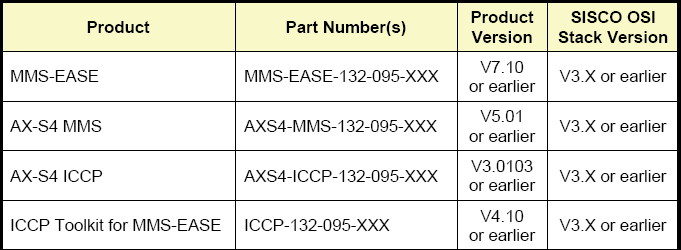
|
|
Vendor Information
CVSS Metrics
| Group | Score | Vector |
|---|---|---|
| Base | ||
| Temporal | ||
| Environmental |
References
Acknowledgements
This vulnerability was reported by SISCO.
This document was written by Ryan Giobbi, based on information from SISCO.
Other Information
| CVE IDs: | CVE-2005-4812 |
| Severity Metric: | 0.92 |
| Date Public: | 2005-02-25 |
| Date First Published: | 2006-09-20 |
| Date Last Updated: | 2008-07-21 20:04 UTC |
| Document Revision: | 61 |