Overview
A denial-of-service vulnerability exists in the Hot Standby Router Protocol (HSRP) .
Description
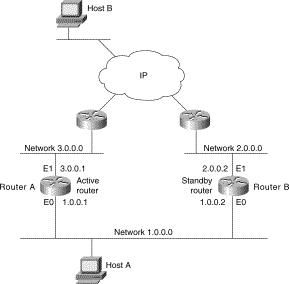
HSRP is a protocol designed to provide transparent recovery of routing services when failures occur. Quoting from RFC2281 (the RFC describing the Hot Standby Router Protocol): The Hot Standby Router Protocol, HSRP, provides a mechanism which is designed to support nondisruptive failover of IP traffic in certain circumstances. In particular, the protocol protects against the failure of the first hop router when the source host cannot learn the IP address of the first hop router dynamically. The protocol is designed for use over multi-access, multicast or broadcast capable LANs (e.g., Ethernet). HSRP is not intended as a replacement for existing dynamic router discovery mechanisms and those protocols should be used instead whenever possible . A large class of legacy host implementations that do not support dynamic discovery are capable of configuring a default router. HSRP provides failover services to those hosts. |
Impact
An attacker located on the same LAN segment as the routers using HSRP can disrupt legitimate network traffic resulting in a denial-of-service attack against the network infrastructure for which the participating routers are responsible for. |
Solution
The CERT/CC is currently unaware of a practical solution to this problem. |
Workaround
|
Vendor Information
CVSS Metrics
| Group | Score | Vector |
|---|---|---|
| Base | ||
| Temporal | ||
| Environmental |
References
- http://www.faqs.org/rfcs/rfc2281.html
- http://www.securityfocus.com/bid/2684
- http://www.cisco.com/warp/public/619/3.html
- http://www.cisco.com/warp/public/619/hsrpguidetoc.html
- http://www.cisco.com/univercd/cc/td/doc/product/software/ios121/121cgcr/ip_c/ipcprt1/1cdip.htm#xtocid1715023
- http://www.cisco.com/univercd/cc/td/doc/cisintwk/ics/cs009.htm#xtocid122331
Acknowledgements
The CERT/CC thanks Cisco Systems for their help in understanding this vulnerability.
This document was written by Ian A. Finlay.
Other Information
| CVE IDs: | CVE-2001-0741 |
| Severity Metric: | 6.33 |
| Date Public: | 1998-03-01 |
| Date First Published: | 2001-12-13 |
| Date Last Updated: | 2001-12-18 13:47 UTC |
| Document Revision: | 85 |